一、背景
购买域名时,提供商都会送免费的SSL证书,此证书只匹配购买的顶级域名(比如1msky.cn)。
而对于二级域名*.1msky.cn来说是不匹配的,如果要购买价格是十分昂贵的,
对于个人站点来说并不是必须的本文章给大家介绍一个申请通配符SSL证书的方法。
此证书有效期 90天, 要到期时, 需要重新申请, 并替换至站点。
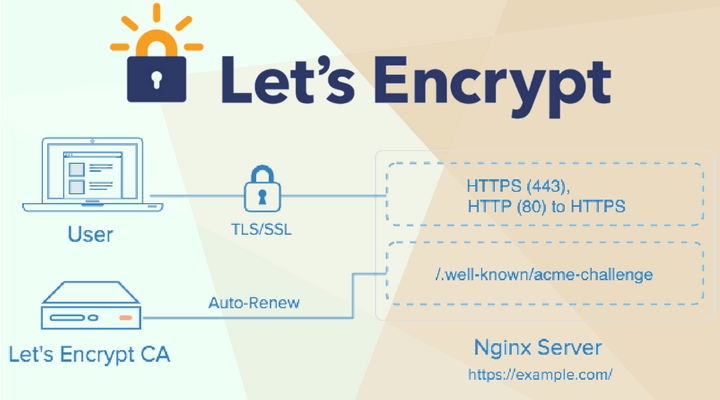
二、效果
访问站点url从http://1msky.cn变成https://1msky.cn。
浏览器地址栏显示安全,有一小锁。
HTTP + SSL = HTTPS的意义在于,站点配置了SSL证书之后,
可以确保用户在浏览器上输入的相关信息及从服务器上查询的信息都是以加密的形式传输,
而且是不可能被非法篡改和窃取的,所以可以充分保障网站数据的传输安全。
三、生成SSL证书并导入
ACME全称 The Automatic Certificate Management Environment。
acme.sh脚本,则能够在Linux上实现如下功能:
- 自动向Let's Encrypt申请证书
本文介绍 - 自动调用各大云平台的api接口实现TXT解析配置
下篇介绍 - 证书下发后自动部署到nginx
下篇介绍 - 利用定时器,每60天自动更新证书,并完成自动部署
下篇介绍
本文采用DNS验证来生成SSL证明书
1. 下载acme.sh,输入命令安装
下载密码(评论刷新后可见)
将脚本放到linux系统,输入如下命令安装
chmod u+x acme.sh
./acme.sh INSTALLONLINE=1[root@ofstest ~]# chmod u+x acme.sh
[root@ofstest ~]# ./acme.sh INSTALLONLINE=1
--2019-07-03 21:43:02-- https://raw.githubusercontent.com/Neilpang/acme.sh/master/acme.sh
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 151.101.108.133
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|151.101.108.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 189239 (185K) [text/plain]
Saving to: ‘STDOUT’
100%[===========================================================================>] 189,239 --.-K/s in 0.09s
2019-07-03 21:43:02 (2.09 MB/s) - written to stdout [189239/189239]
[Wed Jul 3 21:43:02 CST 2019] Installing from online archive.
[Wed Jul 3 21:43:02 CST 2019] Downloading https://github.com/Neilpang/acme.sh/archive/master.tar.gz
[Wed Jul 3 21:43:03 CST 2019] Extracting master.tar.gz
[Wed Jul 3 21:43:03 CST 2019] It is recommended to install socat first.
[Wed Jul 3 21:43:03 CST 2019] We use socat for standalone server if you use standalone mode.
[Wed Jul 3 21:43:03 CST 2019] If you don't use standalone mode, just ignore this warning.
[Wed Jul 3 21:43:03 CST 2019] Installing to /root/.acme.sh
[Wed Jul 3 21:43:03 CST 2019] Installed to /root/.acme.sh/acme.sh
[Wed Jul 3 21:43:03 CST 2019] Installing alias to '/root/.bashrc'
[Wed Jul 3 21:43:03 CST 2019] OK, Close and reopen your terminal to start using acme.sh
[Wed Jul 3 21:43:03 CST 2019] Installing alias to '/root/.cshrc'
[Wed Jul 3 21:43:03 CST 2019] Installing alias to '/root/.tcshrc'
[Wed Jul 3 21:43:03 CST 2019] Installing cron job
44 0 * * * "/root/.acme.sh"/acme.sh --cron --home "/root/.acme.sh" > /dev/null
[Wed Jul 3 21:43:03 CST 2019] Good, bash is found, so change the shebang to use bash as preferred.
[Wed Jul 3 21:43:04 CST 2019] OK
[Wed Jul 3 21:43:04 CST 2019] Install success!Install success!说明安装成功。安装的目录在/root/.acme.sh。
2. 输入命令,生成2条TXT解析记录值,来获得验证域名的所有权。
本文以1msky.cn/*.1msky.cn为例子。
cd ~/.acme.sh
./acme.sh --issue --dns \
-d *.1msky.cn -d 1msky.cn \
--yes-I-know-dns-manual-mode-enough-go-ahead-please[root@ofstest .acme.sh]# cd ~/.acme.sh
[root@ofstest .acme.sh]# ./acme.sh --issue --dns -d *.1msky.cn -d 1msky.cn --yes-I-know-dns-manual-mode-enough-go-ahead-please
[Thu Jul 4 22:14:33 CST 2019] Create account key ok.
[Thu Jul 4 22:14:33 CST 2019] Registering account
[Thu Jul 4 22:14:34 CST 2019] Registered
[Thu Jul 4 22:14:34 CST 2019] ACCOUNT_THUMBPRINT='Bya3LQqUjry7Vyhj_breVlG0YKo-UZuyHgFbiHL9YiI'
[Thu Jul 4 22:14:34 CST 2019] Creating domain key
[Thu Jul 4 22:14:34 CST 2019] The domain key is here: /root/.acme.sh/*.1msky.cn/*.1msky.cn.key
[Thu Jul 4 22:14:34 CST 2019] Multi domain='DNS:*.1msky.cn,DNS:1msky.cn'
[Thu Jul 4 22:14:34 CST 2019] Getting domain auth token for each domain
[Thu Jul 4 22:14:36 CST 2019] Getting webroot for domain='*.1msky.cn'
[Thu Jul 4 22:14:36 CST 2019] Getting webroot for domain='1msky.cn'
[Thu Jul 4 22:14:36 CST 2019] Add the following TXT record:
[Thu Jul 4 22:14:36 CST 2019] Domain: '_acme-challenge.1msky.cn'
[Thu Jul 4 22:14:36 CST 2019] TXT value: 'TnYC60byPOellN3YvrTOpj7SnZRT6vvP1MjFK2MQV7s'
[Thu Jul 4 22:14:36 CST 2019] Please be aware that you prepend _acme-challenge. before your domain
[Thu Jul 4 22:14:36 CST 2019] so the resulting subdomain will be: _acme-challenge.1msky.cn
[Thu Jul 4 22:14:36 CST 2019] Add the following TXT record:
[Thu Jul 4 22:14:36 CST 2019] Domain: '_acme-challenge.1msky.cn'
[Thu Jul 4 22:14:36 CST 2019] TXT value: 'JqgEysREU9-4MOUC3BDWFmSQlVX28Ojt1SUqCK1y9_E'
[Thu Jul 4 22:14:36 CST 2019] Please be aware that you prepend _acme-challenge. before your domain
[Thu Jul 4 22:14:36 CST 2019] so the resulting subdomain will be: _acme-challenge.1msky.cn
[Thu Jul 4 22:14:36 CST 2019] Please add the TXT records to the domains, and re-run with --renew.
[Thu Jul 4 22:14:36 CST 2019] Please add '--debug' or '--log' to check more details.
[Thu Jul 4 22:14:36 CST 2019] See: https://github.com/Neilpang/acme.sh/wiki/How-to-debug-acme.sh记录下2条TXT解析记录(备用)
TXT value: TnYC60byPOellN3YvrTOpj7SnZRT6vvP1MjFK2MQV7s
Domain: _acme-challenge.1msky.cn
TXT value: JqgEysREU9-4MOUC3BDWFmSQlVX28Ojt1SUqCK1y9_E
3. 解析记录加入到域名解析
登陆腾讯云域名解析官网,添加上面2条记录。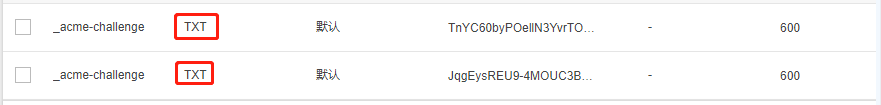
4. 等TTL时间后验证下,输入命令确认TXT记录是否生效。
dig TXT _acme-challenge.1msky.cn +nocomments[root@ofstest .acme.sh]# dig TXT _acme-challenge.1msky.cn +nocomments
; <<>> DiG 9.9.4-RedHat-9.9.4-74.el7_6.1 <<>> TXT _acme-challenge.1msky.cn +nocomments
;; global options: +cmd
;_acme-challenge.1msky.cn. IN TXT
_acme-challenge.1msky.cn. 60 IN TXT "JqgEysREU9-4MOUC3BDWFmSQlVX28Ojt1SUqCK1y9_E"
_acme-challenge.1msky.cn. 60 IN TXT "TnYC60byPOellN3YvrTOpj7SnZRT6vvP1MjFK2MQV7s"
;; Query time: 605 msec
;; SERVER: 172.31.0.2#53(172.31.0.2)
;; WHEN: Thu Jul 04 22:58:40 CST 2019
;; MSG SIZE rcvd: 277有出现2个刚刚追加的TXT值就说OK,接着下一步。
5. 生成证书
./acme.sh --renew \
-d *.1msky.cn -d 1msky.cn \
--dns \
--yes-I-know-dns-manual-mode-enough-go-ahead-please[root@ofstest .acme.sh]# ./acme.sh --renew -d *.1msky.cn -d 1msky.cn --dns --yes-I-know-dns-manual-mode-enough-go-ahead-please
[Thu Jul 4 23:16:02 CST 2019] Renew: '*.1msky.cn'
[Thu Jul 4 23:16:02 CST 2019] Skip, Next renewal time is: Mon Sep 2 15:13:57 UTC 2019
[Thu Jul 4 23:16:02 CST 2019] Add '--force' to force to renew.
[root@ofstest .acme.sh]# ./acme.sh --renew -d *.1msky.cn -d 1msky.cn --dns --yes-I-know-dns-manual-mode-enough-go-ahead-please --force
[Thu Jul 4 23:16:09 CST 2019] Renew: '*.1msky.cn'
[Thu Jul 4 23:16:10 CST 2019] Multi domain='DNS:*.1msky.cn,DNS:1msky.cn'
[Thu Jul 4 23:16:10 CST 2019] Getting domain auth token for each domain
[Thu Jul 4 23:16:12 CST 2019] Getting webroot for domain='*.1msky.cn'
[Thu Jul 4 23:16:12 CST 2019] Getting webroot for domain='1msky.cn'
[Thu Jul 4 23:16:12 CST 2019] *.1msky.cn is already verified, skip dns-01.
[Thu Jul 4 23:16:12 CST 2019] 1msky.cn is already verified, skip dns-01.
[Thu Jul 4 23:16:12 CST 2019] Verify finished, start to sign.
[Thu Jul 4 23:16:12 CST 2019] Lets finalize the order, Le_OrderFinalize: https://acme-v02.api.letsencrypt.org/acme/finalize/60579274/664564827
[Thu Jul 4 23:16:13 CST 2019] Download cert, Le_LinkCert: https://acme-v02.api.letsencrypt.org/acme/cert/03413f9885a460e6256697c93c431b0dc48c
[Thu Jul 4 23:16:14 CST 2019] Cert success.
-----BEGIN CERTIFICATE-----
MIIFVzCCBD+gAwIBAgISA0E/mIWkYOYlZpfJPEMbDcSMMA0GCSqGSIb3DQEBCwUA
MEoxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MSMwIQYDVQQD
ExpMZXQncyBFbmNyeXB0IEF1dGhvcml0eSBYMzAeFw0xOTA3MDQxNDE2MTNaFw0x
OTEwMDIxNDE2MTNaMBUxEzARBgNVBAMMCiouMW1za3kuY24wggEiMA0GCSqGSIb3
DQEBAQUAA4IBDwAwggEKAoIBAQCh+vis3YieGnOQG15upkVE02ImwYLHgK0gh4B5
K6GVI6xeVAxEU3WeUVKOLXiiYimkruvuXo+U4h5tjRtpkZZSl6yh2wQSWSliOEKH
MB7zzkc8ggzrGGeoQsyk2t4+AADrB1+KtVGDj9SSWEcPv3sF/DdQ5TfG0Z+kKYs0
EnXqdqDRNM0xkX70/MAqX4K9vN1MhIwHWa4ga1zWJTSwTQ6vsp5ulY3SCjNq49gJ
3OuZ8ptaC4TuD3ccaBjZhus00P5YsfbLNQSybSj8DOfqEEqT8Tl8laoKXK7DJKsy
CnuOPWimen1jSsTXT27FN2qqxF+iZ1147DDZmFhmVkL7SfDDAgMBAAGjggJqMIIC
ZjAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMC
MAwGA1UdEwEB/wQCMAAwHQYDVR0OBBYEFKru4c2EInMfMlaRgQhcw/GoqKLuMB8G
A1UdIwQYMBaAFKhKamMEfd265tE5t6ZFZe/zqOyhMG8GCCsGAQUFBwEBBGMwYTAu
BggrBgEFBQcwAYYiaHR0cDovL29jc3AuaW50LXgzLmxldHNlbmNyeXB0Lm9yZzAv
BggrBgEFBQcwAoYjaHR0cDovL2NlcnQuaW50LXgzLmxldHNlbmNyeXB0Lm9yZy8w
HwYDVR0RBBgwFoIKKi4xbXNreS5jboIIMW1za3kuY24wTAYDVR0gBEUwQzAIBgZn
gQwBAgEwNwYLKwYBBAGC3xMBAQEwKDAmBggrBgEFBQcCARYaaHR0cDovL2Nwcy5s
ZXRzZW5jcnlwdC5vcmcwggEFBgorBgEEAdZ5AgQCBIH2BIHzAPEAdgB0ftqDMa0z
EJEhnM4lT0Jwwr/9XkIgCMY3NXnmEHvMVgAAAWu9jq/6AAAEAwBHMEUCIEyyMmU0
/o1aW2pNul7bFo4cdx6vvH1CP7WPAzhFEKEbAiEA2sLhagBNitd7tahFORYMr8vZ
WJc26B5mb8IGRAxKsXAAdwApPFGWVMg5ZbqqUPxYB9S3b79Yeily3KTDDPTlRUf0
eAAAAWu9jq/oAAAEAwBIMEYCIQDonOc7fMr+lrdJeJf9vp4OAWqr+iag5nB6PgXp
zSoeegIhALI5rclA7T+nWMdoSUt4wXgHdlwrg/AsJcylTHnJfmK/MA0GCSqGSIb3
DQEBCwUAA4IBAQA77XSbtjZihwgtMqHRJMVdjEXhrNV8kzfpMfau1TCAnp1nx0mB
66VAei/KLuu/39ltWWf5pZR27Yu1teTKp6uzOzwEEQD6J3XGUKwCjcsUyg8cGgeH
uGbkU8CwJoRz3Un5fkz6We9NAUsHDwLX6Zi+4l87xqLh8/aORxMIeRg4d3ZjeK7b
dYiZYsYtUDbB+kWP1h2EUoNQ7QNN9rqtVnxT+tp+5v+LVB55CetTMFLODNnPimXx
LiHVIWo5/GP+dlUCCkguAlNh73M4TEN5fT/s6ggLIaB4cghAEKUwSsM3YC9Eh0eY
voJJ+FWG5JkTgcDHfWa1UFUB3VliOE9QEj3K
-----END CERTIFICATE-----
[Thu Jul 4 23:16:14 CST 2019] Your cert is in /root/.acme.sh/*.1msky.cn/*.1msky.cn.cer
[Thu Jul 4 23:16:14 CST 2019] Your cert key is in /root/.acme.sh/*.1msky.cn/*.1msky.cn.key
[Thu Jul 4 23:16:14 CST 2019] The intermediate CA cert is in /root/.acme.sh/*.1msky.cn/ca.cer
[Thu Jul 4 23:16:14 CST 2019] And the full chain certs is there: /root/.acme.sh/*.1msky.cn/fullchain.cer
[Thu Jul 4 23:16:14 CST 2019] It seems that you are using dns manual mode. please take care: The dns manual mode can not renew automatically, you must issue it again manually. You'd better use the other modes instead.
[Thu Jul 4 23:16:14 CST 2019] Call hook error.
[root@ofstest *.1msky.cn]# ll
total 28
-rw-r--r-- 1 root root 1911 Jul 4 23:16 *.1msky.cn.cer
-rw-r--r-- 1 root root 553 Jul 4 23:16 *.1msky.cn.conf
-rw-r--r-- 1 root root 976 Jul 4 23:16 *.1msky.cn.csr
-rw-r--r-- 1 root root 218 Jul 4 23:16 *.1msky.cn.csr.conf
-rw-r--r-- 1 root root 1675 Jul 4 23:10 *.1msky.cn.key
-rw-r--r-- 1 root root 1648 Jul 4 23:16 ca.cer
-rw-r--r-- 1 root root 3559 Jul 4 23:16 fullchain.cer证书生成完了,目录~/.acme.sh/*.1msky.cn/下
6. 配置nginx加载证书
vim /etc/nginx/nginx.confserver {
listen 443;
server_name localhost;
ssl on;
root html;
index index.html index.htm;
ssl_certificate /etc/nginx/ssl/fullchain.cer;
ssl_certificate_key /etc/nginx/ssl/*.1msky.cn.key;
ssl_session_timeout 5m;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
location / {
root html;
index index.html index.htm;
}
}ssl on;
ssl_certificate /etc/nginx/ssl/fullchain.cer;
ssl_certificate_key /etc/nginx/ssl/*.1msky.cn.key;
7. 证书拷贝到指定目录,并重启Nginx。
./acme.sh --installcert -d *.1msky.cn \
--key-file /etc/nginx/ssl/*.1msky.cn.key \
--fullchain-file /etc/nginx/ssl/fullchain.cer \
--reloadcmd "service nginx force-reload"[root@ofstest .acme.sh]# ./acme.sh --installcert -d *.1msky.cn \
> --key-file /etc/nginx/ssl/*.1msky.cn.key \
> --fullchain-file /etc/nginx/ssl/fullchain.cer \
>
[Thu Jul 4 23:37:15 CST 2019] Installing key to:/etc/nginx/ssl/*.1msky.cn.key
[Thu Jul 4 23:37:15 CST 2019] Installing full chain to:/etc/nginx/ssl/fullchain.cer
[root@ofstest .acme.sh]# cd /etc/nginx/ssl/
[root@ofstest ssl]# ll
total 8
-rw------- 1 root root 1675 Jul 4 23:37 *.1msky.cn.key
-rw-r--r-- 1 root root 3559 Jul 4 23:37 fullchain.cer四、确认
最后访问确认网页是否安全,有木有小锁。
顶级域名 https://1msky.cn
二级域名 https://image.1msky.cn or https://www.1msky.cn
五、结语
其实acme.sh真正强大的地方还不止这些。DNS方式可以直接调用域名解析提供商上的API添加TXT记录并验证,
目前集成了DNSPOD,CloudFlare, Cloudxns, Godady等提供商的API。
最后,通过设定一个crontab可以定期检查证书是否要过期,
如果即将过期,自动重新申请证书,替换并重启web服务。



密码
学习
学习,谢谢
学习
好厉害哦OωO
学习
踩下
OωO